Playbook for data loss – data breach – information leakage
Summary
If short on time directly jump to the playbooks section.
A data breach comes as a result of a cyber attack that allows cyber criminals to gain unauthorized access to a computer system or network and steal the private, sensitive, or confidential personal and financial data of the customers or users contained within. Information leakage can also happen by an insider intentionally or unintentionally.
Incident Communication becomes one of the most critical first steps. Next higher priority questions: “How did the breach take place?” and “What customer data is affected?”.
Recognize if it is a PRIVACY-related incident. If personal data is compromised immediately adhere to the country specific regulations. Involve management, legal, HR and PR in the escalated incident.
Overview of a data breach at – https://www.malwarebytes.com/data-breach/
Case Study – Communication perspective
Thanks to Medibank for the regular updates ensured to the stakeholders. Observe the complete timeline (Please start from bottom of page to the top) – https://www.medibank.com.au/health-insurance/info/cyber-security/timeline/
Below are the nice learnings to adopt
- Announcement of the incident on the company website. And the same followed in other media.
- Summary of the incident
- What happened
- What we’ve done in response:
- Our focus moving forward
- Periodic announcement update to all the stakeholders, customers via email.
- Frequently asked questions
- How can I update my personal details?
- Do I need to update my payment details?
- What details have been accessed?
- When will I know if my data has been accessed or stolen?
- What should I do if my details have been accessed or stolen?
- How are you supporting affected customers?
Playbook to respond in a structured way
FlexibleIR provides you with different flavors of best practice playbooks for the same threat. This will help to get multiple perspectives to handle today’s complex targeted attacks. You can build state-of-the-art playbooks combining these playbooks and your operational knowledge.

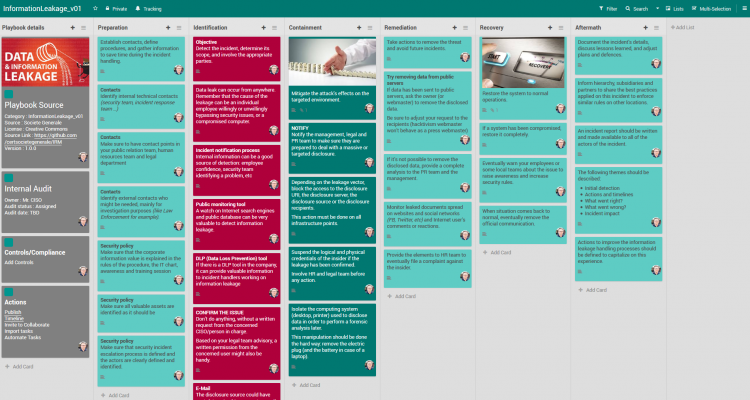
- Some more reference playbooks
- https://www.bankinfosecurity.com/to-survive-data-breach-create-response-playbook-a-13459
- https://www.bankinfosecurity.com/surviving-breach-8-incident-response-essentials-a-13460
- Experian data breach response guide
Mitigations
Please refer to the detailed playbooks above.
- Here is also what a few experts recommend based on their experiences: Digital Guardian Blog
Breach Response Templates
Refer – https://playbooks.flexibleir.com/cyber-incident-breach-communication-or-disclosure-templates/
Analysis
Identification & Scoping of the incident is key. Please refer to the playbooks above.
Cloud and container security notes
- Under protected APIs
- Unlimited access to APIs
- Many APIs only check authentication status, but not which user is authenticated
- Session management-related attacks
- FAILURE TO CONFIGURE OR IMPLEMENT CORS
- Issues related to input validation
- Open and insecure S3 buckets
Tips
Know whom to call. Please first ensure you are able to quickly mobilize all the help required and that the right contacts have been reached out to. You may need to start on several parallel investigation trails. General actions to Recover If Impacted– Don’t Let a Bad Day Get Worse.
- Ask for help! Contact CISA, the FBI, or the Secret Service (If in US) . Respective CERTs for every country.
- Work with an experienced advisor to help recover from a cyber attack
- Isolate the infected systems and phase your return to operations
- Review the connections of any business relationships (customers, partners, vendors) that touch your network
- Apply business impact assessment findings to prioritize recovery
- Fact – how the attackers got access – will likely take time to determine. So have parallel tracks running for immediate containment and investigative/forensic works.
References
References
Latest incidents & learning
https://www.safetydetectives.com/blog/cam-leak-report/
Innovations
Thinking out of the box is key when a major breach has happened and everything is down. Here is an example of creative thinking down at HYDRO during their incident remediation phase.
Automation
Consider possible automation candidate scripts to reduce impact time.
User Contributed Notes
FlexibleIR aims to provide state-of-the-art playbooks by utilizing the power of the community to build on quality playbooks. Readers add their operation knowledge and thoughts to make every playbook evolving and better.
Revisions
July 27, 2023 : Case Study added
March 13, 2020: Initial Version
