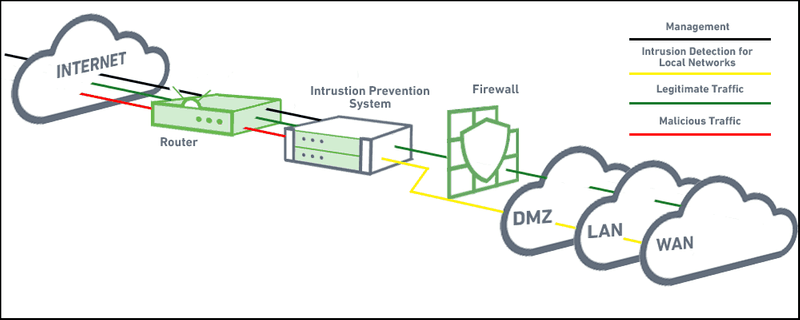
Playbook for Malicious Network Behavior: Malicious Traffic
Alerts are generated when something suspicious is seen by one of the Network monitoring devices. Network Security Tools:IDS (Intrusion Detection System)IPS (Intrusion Prevention System)DLP (Data Loss Prevention)SIEM (Security Incident and Event Management)NBAD (Network Behavior Anomaly Detection) Playbook Mitigation https://cert.societegenerale.com/resources/files/IRM-5-Malicious-Network-Behaviour.pdf References