April 9, 2020
Playbook for Insider Threat
Summary
Insider threats are growing and are very complex to handle as it needs to be worked out very closely with a lot of stakeholders including the human resource department.
Our special thanks to Prof. Monica Whitty[1]
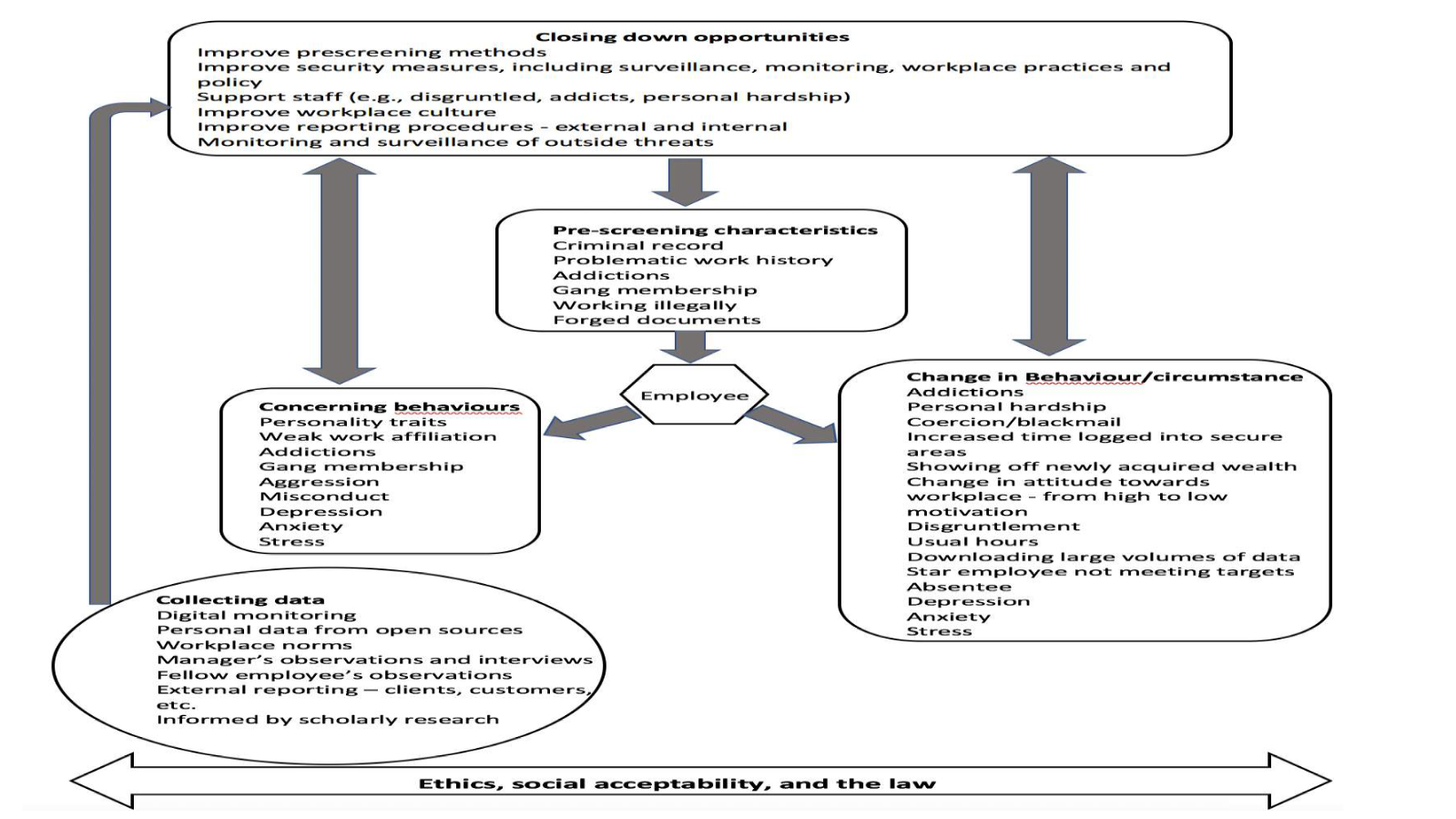
Playbook

Technical details
USE CASES
- Theft
- IP theft – e.g., company secrets, money, data
- Fraud (High ~-70%)
- Terrorism
- Reputation damage
- Blackmail
- Denial of service attacks
- Introduction of viruses, worms Trojan horses
- Corruption or deletion of data
- Altering data
- Password cracking
BEHAVIOURAL INDICATORS
- Hypothetical situations – language change + negative affect (Taylor et al., 2013)
- Emotional state, such as depressed, stressed (e.g., Shaw & Stock, 2011; Turner & Gelles, 2003).
- IP theft: Volume of printing (Malood & Stephens, 2007).
DISCOVERY
- Digital/video evidence – Digital or cyber evidence obtained after the attack because suspicions had been raised
- Monitoring physical/online initiated after the attack – The person was monitored more closely after complaints or suspicions (usually from someone outside of the organisation). The attack was then discovered in real-time and evidence was found of previous attacks
- Monitoring procedures real time – Monitoring procedures detected the attack in real time (cyber and/or physical).
- Customer complaints – Serious complaints by clients/customers about the employee or about problems with their accounts prompted an investigation.
- Suspicious behaviours reported – Suspicious behaviour/caught in the act reported by fellow employees prompted an investigation.
- Outside organisation – An outside organisation detected the attack – the evidence was provided via these outside sources, which prompted an internal investigation.
Mitigation
Please refer to the playbook above.
Analysis
References
https://www.techradar.com/news/online-game-popular-with-millions-of-children-gets-compromised
Whitty, M. T. (in press). Developing a conceptual model for insider threat. Journal of Management & Organization.
https://www.youtube.com/watch?v=Zdqy_qgPUfA
Revisions
March 13, 2020: Initial Version