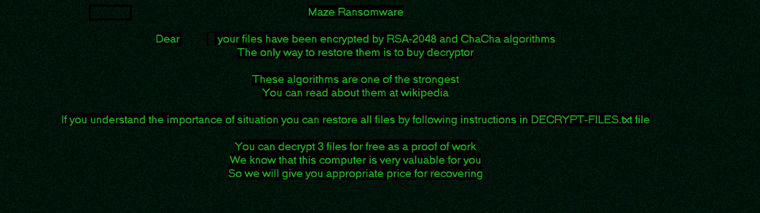
Playbook for Maze Ransomware
You need to quickly contain the problem considering which part of kill chain your adversary is in. You to need contain and neutralize the impact of the incident by possibly shutting down specific services/servers/segments.