Playbook for Phishing
If short on time directly jump to the playbooks section.
Summary
Any attempt to compromise a system and/or steal information by tricking a user into responding to a malicious message. The most common phishing attacks involve emails armed with malware hidden in attachments or links to infected websites, although phishing can be conducted via other methods such as voicemail, text messages, and social media, too.
Playbook
FlexibleIR provides you with different flavors of best practice playbooks for the same threat. This will help to get multiple perspectives to handle today’s complex targeted attacks. You can build state-of-the-art playbooks combining these playbooks and your operational knowledge.

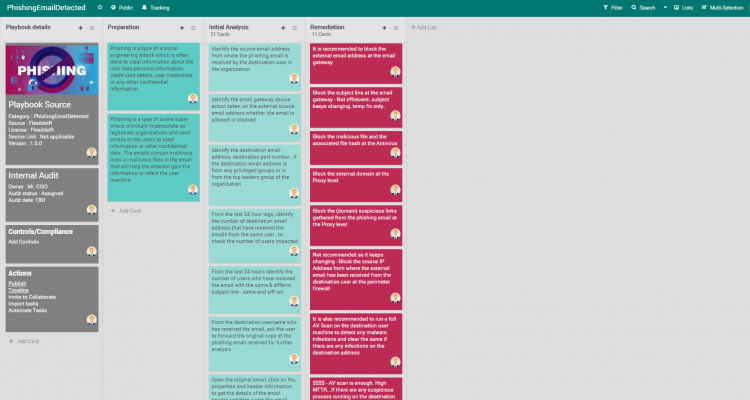
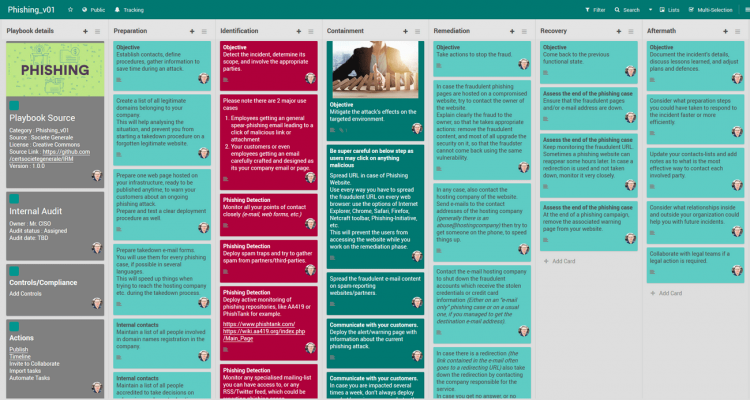
- Some more reference playbooks
- https://www.incidentresponse.com/playbooks/phishing
- https://www.demisto.com/phishing-incident-response-playbook/
- Government of Scotland
- https://www.ncsc.gov.uk/guidance/phishing – Please also see the case study
- https://github.com/counteractive/incident-response-plan-template/blob/master/playbooks/playbook-phishing.md
Mitigations
Please refer to the detailed playbooks above.
Analysis
Identification & Scoping of the incident is key. Please refer to the playbooks above.
Tips
Know whom to call. Please first ensure you are able to quickly mobilize all the help required and the right contacts have been reached out to. You may need to start on several parallel investigation trails. General actions to Recover If Impacted– Don’t Let a Bad Day Get Worse.
- Ask for help! Contact CISA, the FBI, or the Secret Service (If in US) . Respective CERTs for every country.
- Work with an experienced advisor to help recover from a cyber attack
- Isolate the infected systems and phase your return to operations
- Review the connections of any business relationships (customers, partners, vendors) that touch your network
- Apply business impact assessment findings to prioritize recovery
- Fact – how the attackers got access – will likely take time to determine. So have parallel tracks running for immediate containment and investigative/forensic works.
References
References
PerSwaysion Campaign – Microsoft Document Sharing
https://resources.infosecinstitute.com/topics/phishing/#gref
Latest incidents & learning
- Intresting twitter phishing campaign – Link 06 Dec, 2021
- Deepsource – Spearphising attack by Sawfish
- Containment – Within two hours, DeepSource rotated all its users’ tokens, client secrets, and private keys, as well as “all credentials and keys of employees who had access to production systems.”
- Github accounts stolen – Ongoing phishing attacks
- Reset password immediately.
- Reset two-factor recovery codes immediately.
- Review personal access tokens.
- Take additional steps to review and secure their accounts.
Automation
Consider possible automation candidate scripts to reduce impact time.
User Contributed Notes
FlexibleIR aims to provide state-of-the-art playbooks by utilizing the power of the community to build on quality playbooks. Readers add their operation knowledge and thoughts to make every playbook evolving and better.
In this playbook the following mitigation steps are missing:
- Check for DMARC protocol.
- Add use cases for Outlook365 BEC
Revisions
March 13, 2020: Initial Version
This playbook the following mitigation steps are missing:
1. Check for DMARC protocol.
2. Add use cases for Outlook365 BEC
[…] venkat on Playbook for Phishing […]