Playbook for a Ransomware Attack
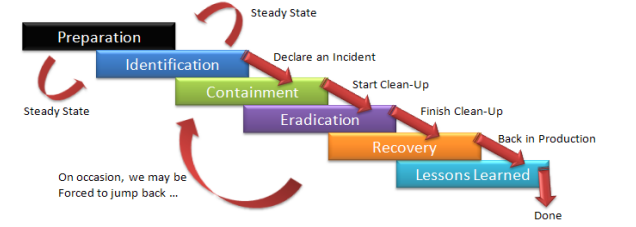
If under attack, quickly do the scoping and plan for containment. Download an Authoritative Write-Up (if available) for the Specific Ransomware Variant(s) Encountered. Harvest additional Indicators from the Report(s). Mobilize the team and remember to take as much help as possible. Ransomware operations will mostly have similar patterns of attack frameworks, tools, and techniques across victims. They will also have similar operations as other Ransomware […]