Playbook for a Ransomware Attack
If under attack, quickly do the scoping and plan for containment. Download an Authoritative Write-Up (if available) for the Specific Ransomware Variant(s) Encountered. Harvest additional Indicators from the Report(s). Mobilize the team and remember to take as much help as possible.
Ransomware operations will mostly have similar patterns of attack frameworks, tools, and techniques across victims. They will also have similar operations as other Ransomware families like Ryuk, DoppelPaymer. The same applies to Affiliates and Actors who could use a whole range of Ransomware flavors and possibly their Playbooks for operating. Summary – quickly understand their overall pattern of operation.
The main goal of ransomware is to crypt all files that it can in an infected system and then demand a ransom to recover the files. However, the most important characteristic of Maze is the threat that the malware authors give to the victims that, if they do not pay, they will release the information on the Internet[2].
Details on general ransomware are available at – Link.
Playbook for a generic Ransomware attack
FlexibleIR provides you with different flavors of best practice playbooks for the same threat. This will help to get multiple perspectives to handle today’s complex targeted attacks. You can build state-of-the-art playbooks combining these playbooks and your operational knowledge.
To customize the below playbook, login to our platform, customize and download playbook in formats of your choice. For subscription please contact us.
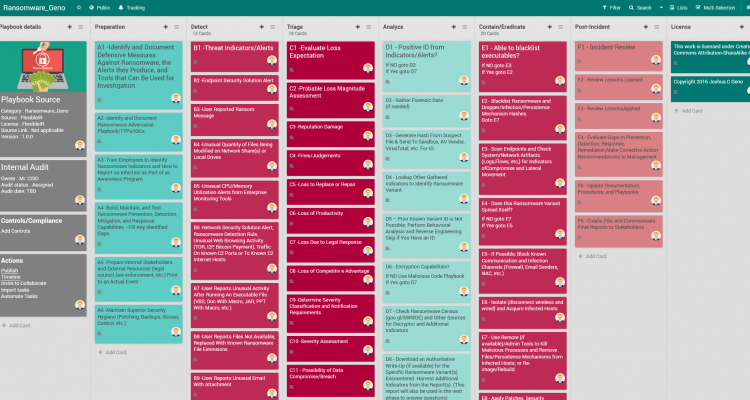
Our sincere thanks to Joshua C Geno for the above playbook. Please mail us in case you need an original version of the pdf file at contact@flexibleir.com


FlexibleIR helps you build you own Ransomware playbook suiting your needs
- FlexibleIR provides a system where you can build your own Playbook by yourself.
- We also provide you with subject matter experts (SMEs) to build your playbooks
- Please feel free to contact us – contact@flexibleir.com
Technical Details of adversary
Understanding your adversary is half battle won. Here is an example of Maze Ransomware at: https://www.mcafee.com/blogs/other-blogs/mcafee-labs/ransomware-maze/ (look at IoCs)
- TTPs – Mitre Att&ck matrix
- Most important – https://attack.mitre.org/software/S0449/
- See above in Mitre Navigator too
- Note that the initial access would be through Phishing or a exploit kit
- https://unit42.paloaltonetworks.com/threat-brief-maze-ransomware-activities/
- Fireeye threat research
Mitigations
The containment strategy (Remediation / Stop the spread) is based on the below tactics used by the adversary[5]
- STOP: Lateral dispersion amongst systems using standard Windows Operating System protocols
- Endpoint Segmentation – Hardening – Windows Firewall
- RDP Hardening – Enforce Multi-Factor Authentication – Leverage Network Level Authentication – Restrict Administrative Accounts from Leveraging RDP on Internet-Facing Systems
- STOP: Lateral dispersion amongst systems via binding to administrative shares for tool or malware deployment (eg. • ADMIN$• C$• D$• IPC$)
- Disable Administrative / Hidden Shares – Registry Method – Group Policy Method
- STOP: Lateral dispersion amongst systems via vulnerability exploitation or legacy protocol abuse
- Disable SMB v1 – PowerShell Method – Registry Method – Group Policy Method
- STOP: Lateral dispersion between systems via Windows Remote Management (WinRM) and PowerShell remoting
- Hardening Windows Remote Management (WinRM) – PowerShell – Group Policy Method
- STOP: Lateral movement and propagation using the built-in local administrator account on endpoints
- Remote Usage of Local Accounts – SIDs within Group Policy settings
- STOP: Lateral movement and propagation using domain-based accounts
- Reduce the Exposure of Privileged and Service Accounts – Privileged Account Logon Restrictions – Service Account Logon Restrictions – Protected Users Security Group
- STOP: Obtaining cleartext credentials in memory for credential harvesting
- Cleartext Password Protections – Registry Method – Group Policy Method
Analysis
Identification & Scoping of the incident is key. Look at the IoCs[5] and ensure you know the ransomware-type and the variant. Please note there are new variants released every second.
Key Link from Fireye[5].
Identify which of the below 2 common techniques is used by the Ransomware to deploy across your environment
- Manual propagation by a threat actor after they have penetrated an environment and have administrator-level privileges broadly across the environment:
- Manually run encryptors on targeted systems.
- Deploy encryptors across the environment using Windows batch files (mount C$ shares, copy the encryptor, and execute it with the Microsoft PsExec tool).
- Deploy encryptors with Microsoft Group Policy Objects (GPOs).
- Deploy encryptors with existing software deployment tools utilized by the victim organization.
- Automated propagation
- Credential or Windows token extraction from disk or memory.
- Trust relationships between systems — and leveraging methods such as Windows Management Instrumentation (WMI), SMB, or PsExec to bind to systems and execute payloads.
- Unpatched exploitation methods (e.g., EternalBlue — addressed via Microsoft Security Bulletin MS17-010).
Preparation
Practise, Practise, and Practise before the crisis happens. Go through case studies of Ransomware attacks.
Walkthrough specific events. Here is an example – Surviving a Ransomware Attack – Lessons from the Field
Tips
Know whom to call. Please first ensure you are able to quickly mobilize all the help required and the right contacts have been reached out to. You may need to start on several parallel investigation trails. General actions to Recover If Impacted– Don’t Let a Bad Day Get Worse.
- Ask for help! Contact CISA, the FBI, or the Secret Service (If in US) . Respective CERTs for every country.
- Work with an experienced advisor to help recover from a cyber attack
- Isolate the infected systems and phase your return to operations
- Review the connections of any business relationships (customers, partners, vendors) that touch your network
- Apply business impact assessment findings to prioritize recovery
- Fact – how the attackers got access – will likely take time to determine. So have parallel tracks running for immediate containment and investigative/forensic works.
Variants
Ensure you are not looking at older mitigations or IoCs.
References
References
IoCs
https://www.cert-in.org.in/s2cMainServlet?pageid=PUBVA01&VACODE=CIVA-2020-1674
https://cert.ssi.gouv.fr/ioc/CERTFR-2020-IOC-001/
https://www.us-cert.gov/ncas/alerts/TA16-091A
https://www.us-cert.gov/Ransomware
https://www.fbi.gov/file-repository/ransomware-prevention-and-response-for-cisos.pdf
Low
https://www.infrascale.com/wp-content/uploads/pdf/Infrascale-Steps-to-Mitigate-Ransomware.pdf
https://logrhythm.com/blog/5-steps-to-defend-against-ransomware/
Advanced
https://www.crowdstrike.com/blog/maze-ransomware-deobfuscation/
Incidents
Decryptor
Ensure to have a clear test setup. Consider trying out a decryptor to regain access to files. The decryptor may or may not work to unlock.
Innovations
Thinking out of the box is key when everything is down. Here is an example of creative thinking down at HYDRO during their incident remediation phase.
Automation
Consider possible automation candidate scripts to reduce impact time.
User Contributed Notes
Revisions
Sept 02, 2021: Initial Version