Playbook for Malware outbreak
If short on time directly jump to the playbooks section.
The Malware (Malicious code) response procedures will include validating malware, understanding the impact, and determining the best containment approach. The remediation process ends with containing and removing the malware from systems. The spread of the malware has to be contained.
Today its all multi-staged attacks. Your initial stage analysis could be a clue to a major attack in progress.
- Identify if recently has been observed on other systems or you see a widespread alert
- Identify if active Command and Control (C2) activity of the malware is detected
- Identify if its on privileged user’s system
- Identify if its a targeted attack.
- Internal reconnaissance or exploitation activity detected
- Lateral movement detected
- Credential harvesting tools or output detected
- Anomalous outbound data flow
- Unauthorized software installation
- Key is to understand the “Strike Zone” criteria indicating the appropriate time to take remediating action – stop or contain and bring in your Business Continuity Plan (BCP)
- If ransomware (in particular human operated) – refer to our Ransomware playbook for strategy eg maze
Preferably all investigation and analysis activities must be performed in a lab environment with limited internet connectivity or a dedicated internet connection that is not attributable, to ensure the perpetrators are not made aware that they have been discovered. Most often the method of infection is through a phishing email.
Malicious code refers to all software or otherwise executable instructions on a computer, device or information system with the specific purpose of malicious activity, destruction, or are primarily leveraged to facilitate other malicious activity.
Playbook
FlexibleIR provides you different flavors of best practice playbooks for the same threat. This will help to get multiple perspectives to handle today’s complex targeted attacks. You can build state-of-the-art playbooks combining these playbooks and your operational knowledge.

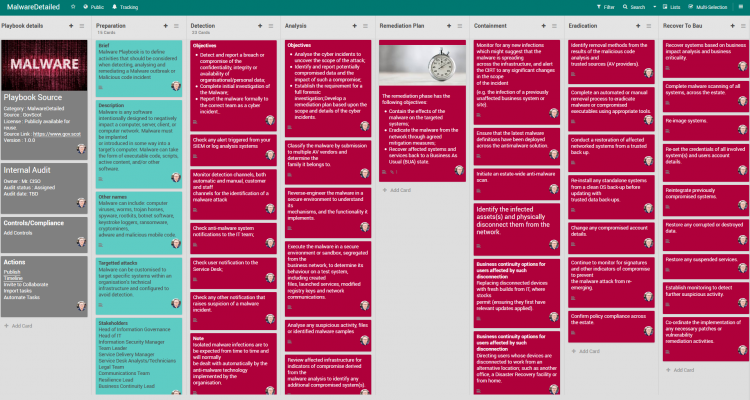


Mitigations
- Determine Containment Procedures
- Determine the appropriate network containment methodologies that will prevent the malware from communicating with the attacker infrastructure and from spreading further throughout the network.
- Identify the infection vector and validate that all controls would block the attack at every phase. If any control would not prevent the attack at that phase, have the control updated.
- URLs are categorized as a blocked category in the Proxy
- AV has a signature to detect the payload
- Sandboxing technology has detection capabilities
- Email Security would block a future email with the same characteristics
- Implement Containment – Apply containment procedures to all compromised systems at the same time.
- Determine Recovery actions for all systems The following removal procedures should be attempted . A ticket should be created and assigned to IT Ops to action the following requests. The ticket number should be recorded in the investigation record.
- AV Cleanup – Determine if the AV is able to fully clean up and restore the system. If so, provide instructions to IT Ops to update the pattern file on the endpoint and run a scan. IT Ops must provide evidence that the expected malware was detected and cleaned to the IT Security team for verification. A scan result of “Clean” or “No Results” does not mean the system is no longer compromised, and should be verified a second time by the IT Security team.
- Manual Removal – If the AV solution is incapable of removing this particular malware, the IT Security team may determine manual removal methods depending on the malware family. Provide these instructions to the IT Ops to remove the malware.
- Ransomware – If there exist instructions to decrypt the system based on the Ransomware family, attempt to perform the decryption at this time on one test system. If successful, perform the decryption routine on all compromised systems. Otherwise, restore any encrypted data by recovering from backups.
- Re-Image – If the malware is unable to be removed from the machine, instruct IT Ops to have the machine re-imaged.
- Update the Investigation Record The investigation record will be updated with all actions performed.
References
References
https://www.taiwannews.com.tw/en/news/3927869
Revisions
March 13, 2020: Initial Version
this is good