Summary
All social engineering techniques rely on exploiting aspects of human interaction and decision-making known as cognitive biases.
The most common techniques: pretexting, baiting, quid pro quo and tailgating. Phishing attacks also rely upon social engineering.
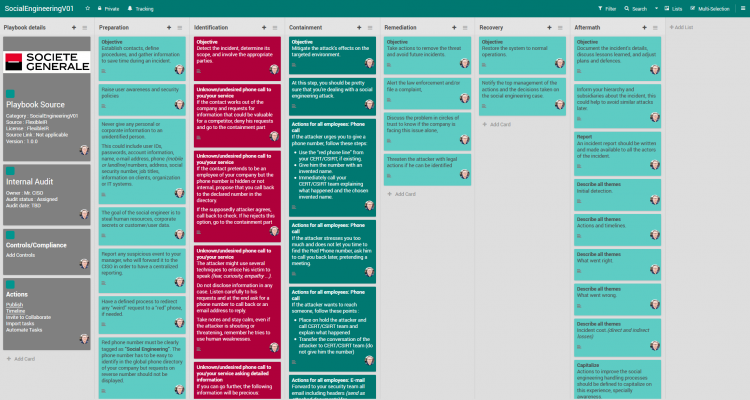
Playbook
Analysis
Will be added soon.
Mitigations
- Coming up soon
References
References
https://www.enisa.europa.eu/topics/csirts-in-europe/glossary/what-is-social-engineering
Revisions
March 13, 2020: Initial Version
Post navigation
Venkat is founder of FlexibleIR. He brings 20 years of experience in building tools and products at Sun Microsystems, Intel, Novell, HP, Yahoo,Tesco and startups. He has developed test suites and frameworks for post silicon validation of the Xeon processor family (Fuzzing). He has worked deeply on UFS files system at SUN Microsystem. Was a security paranoid at Yahoo.