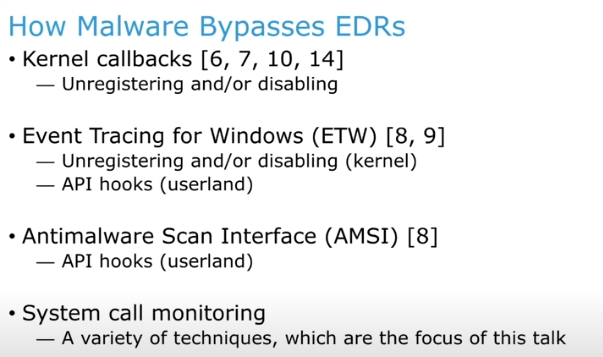
EDR – Tampering by attackers
Problem: Endpoint detection and response (EDR) software has gained significant market share due to its ability to examine system state for signs of malware and attacker activity well beyond what traditional anti-virus software is capable of detecting. This deep inspection capability of EDRs has led to an arms race with malware developers who want to evade EDRs while still achieving desired goals, such as code injection, lateral movement, and credential theft. This monitoring and evasion occurs in the lowest levels of hardware and software, including call stack frames, exception handlers, system calls, and manipulation of native instructions. Given this reality, EDRs are limited in how much lower they can operate to maintain an advantage. The success of EDR bypasses has led to their use in many high-profile attacks and by prolific ransomware groups.
- EDR on all my server machines
- EDR solutions tampered in nearly all ransomware and APT attacks (MITRE ID: T1562.001).
- The first steps attackers take to hide their actions.
- One good example is the Spyboy EDR Killer
- https://github.com/ZeroMemoryEx/Terminator
- Living of the land binaries – https://www.loldrivers.io/
- Develop rules for ransomware TTPs with your SIEM, based on relevant log sources, for example, to detect internal recon, discovery, lateral movement, data exfil or C2 traffic.
- https://detect.fyi/edr-your-weakest-link-in-protecting-against-a-ransomware-attack-14a8cd1ae389
- https://github.com/redcanaryco/atomic-red-team/blob/master/atomics/T1562.001/T1562.001.md
- DEF CON 32 – Defeating EDR Evading Malware with Memory Forensics – Case, Sellers, Richard, et al. – https://www.youtube.com/watch?v=PmqvBe1LSZc
- https://i.blackhat.com/Asia-24/Presentations/Asia-24_Bar-EDREraseDataRemotelyReloaded.pdf
- https://i.blackhat.com/EU-22/Thursday-Briefings/EU-22-Nissan-DirtyVanity.pdf
- https://archive.conference.hitb.org/hitbsecconf2022sin/session/edr-evasion-primer-for-red-teamers/
- https://www.blackhat.com/docs/eu-17/materials/eu-17-Thompson-Red-Team-Techniques-For-Evading-Bypassing-And-Disabling-MS-Advanced-Threat-Protection-And-Advanced-Threat-Analytics.pdf
- KEY – https://github.com/tkmru/awesome-edr-bypass
TODO – Playbook to respond to this alert when detected.