Playbook for DDoS
Attacking or defending against DDoS attacks is very expensive and skill/time intensive. Companies have huge, multi redundant pipes. One of the main reason individuals or syndicates DDOS is to blackmail companies.
If short on time directly jump to the playbooks section.
Please note that DDoS attacks can be rapidly morphing or changing with multiple attack vectors and changing within minutes. The attacker could immediately change the attack once you do a mitigation step.
Stopping a very large DDOS attack takes a data center of operators working with upstream providers to filter out the attack traffic from legitimate traffic. Depending on the size of the attack and the number of attacking sources this can take minutes to weeks.
DDos quick guide from CISA and NIST recommendations to start off your deep dives with.
A slightly old video from Black hat 2013 but gives good lessons learned from spamhaus DDos attack – https://www.youtube.com/watch?v=w04ZAXftQ_Y
Learnings from Proton attack – Black hat – https://www.youtube.com/watch?v=xCG9zA7fq40
Playbook
FlexibleIR provides you with different flavors of best practice playbooks for the same threat. This will help to get multiple perspectives to handle today’s complex targeted attacks. You can build state-of-the-art playbooks combining these playbooks and your operational knowledge.
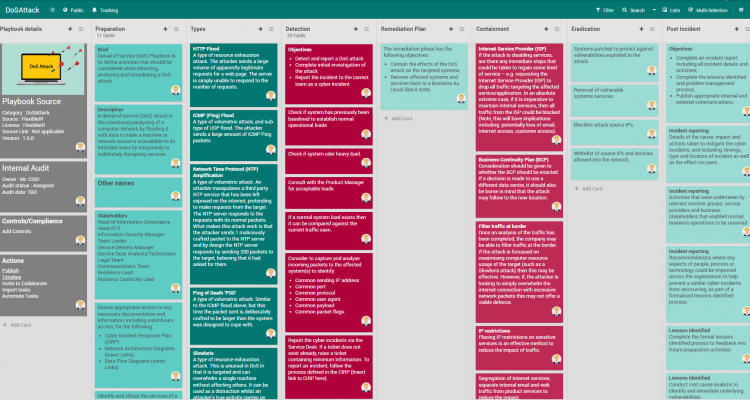

- Some more reference playbooks
Mitigations
Please refer to the detailed playbooks above.
- KEY Recommended MITIGATIONS – https://www.documentcloud.org/documents/7070798-FLASH-MU-000132-DD.html
- Ensure all the contacts with you upstream traffic providers are clearly established. Should be able to interact with them in few minutes.
- Establish a clear communication channel between you Network team, Security team and the Application team.
- Ensure to have clear network diagrams of your infrastructure
- Ensure to know the thresholds of traffic your systems can take. You can do extrapolations based on your baseline data and looking at the various monitoring parameters – CPU/Network/Disk/IO and other detailed OS parameters which can get exhausted – Like number of connections, buffer sizes etc.
- https://www.cyber.nj.gov/mitigation-guides/defending-against-ddos-attacks
- https://www.cyber.nj.gov/this-is-security/ddos-attack-types-and-mitigation-strategies

Amplifications
Below is a sample Amplification. Reference . More details
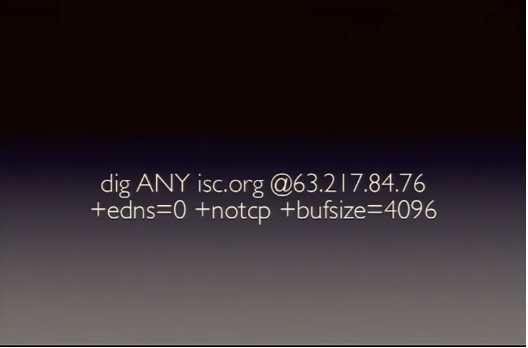
Attacker runs dig or nslookup 
64 bytes data sent 
Large return output from destination 
Large return output 
Sample of Amplification.
Analysis
- Maintain a clear Situational awareness report and Timelines during the whole process.
- Understand what is the source from where the DDos is happening.
- Check Location of the sources – Bulk ip reputation check and the location details
https://www.bulkblacklist.com/ – Put the IPs here and check the reputation - Check the Port number that is being targeted.
- What is the Firewall action? – traffic is allowed
- Check if Single Destination or multiple destinations being targeted
- Check for the criticality of the destination and the application hosted on the destination.
- Ping the destination or check the application is reachable or not
- Check your WAF and IPS signatures – Any DDOS signatures have triggered or not.
- What are the spikes observed as compared with a normal day during the same time
- Traffic could be huge – Consider to block everything at FW level.
- Consideration of GEO based blocking? – IF traffic from a non business location
- Should be in place – DISABLE ICMP at the Firewall level.
Tips
Know whom to call. Please first ensure you are able to quickly mobilize all the help required and the right contacts have been reached out to. You may need to start on several parallel investigation trails. General actions to Recover If Impacted– Don’t Let a Bad Day Get Worse.
- Ask for help! Contact CISA, the FBI, or the Secret Service (If in US) . Respective CERTs for every country.
- Work with an experienced advisor to help recover from a cyber attack
- Review the connections of any business relationships (customers, partners, vendors) that touch your network
- Apply business impact assessment findings to prioritize recovery
References
Latest incidents & learning
November 11, 2021 – https://cisomag.eccouncil.org/ddos-attack-on-voip-provider-telnyx-impacts-global-telephony-services/
https://www.cyber.nj.gov/alerts-advisories/fancy-lazarus-returns-in-another-ransom-ddos-campaign
https://www.link11.com/en/blog/threat-landscape/new-wave-ddos-extortion-campaigns-fancy-lazarus/
https://www.cert.govt.nz/it-specialists/advisories/ddos-extortion-campaign-targeting-financial-sector/
Automation
Consider possible automation candidate scripts to simulate attacks and reduce impact time.
User Contributed Notes
FlexibleIR aims to provide state-of-the-art playbooks by utilizing the power of the community to build on quality playbooks. Readers add their operation knowledge and thoughts to make every playbook evolving and better.
Revisions
June 23, 2021: Initial Version
The remediation steps can have the following:
1. Check Firewall – internal and external
You can add a new use case of DDos – related DNS attacks – with DGA